Unprecedented Exposure of Federal Databases Poses Critical Risk to Every American and National Security
Over 150 government database servers—normally hidden behind layers of security—are now directly exposed to the Internet, leaving Americans' data vulnerable to cyberattacks.
Right now, the US government is experiencing one of history's largest exposures of vulnerability to cyber attacks—and the call's coming from inside the house.
This open-source investigation reveals a massive, completely unprecedented escalation in government database servers—normally hidden behind layers of security—now directly exposed to the Internet. The security of many of these database endpoints is far more lax than even what a small start-up would use. This leaves the door wide open for cybercriminals and spy agencies to steal our most personal information with profound implications for our national security and economy.
Key Findings
Over 2,000 observations of over 150 exposed government database servers in early 2025
655 times when government database servers actively responded to connection attempts
200+ cases involving data replication (port 5022) running from March 7 - 14
54 newly-created or previously-internal endpoints responding to connection attempts
Potential Department of Defense supply chain compromise via a Polish software company
(Cyber wonks, skip to the end to read my methods.)
It’s like if you loudly announced to the world that your house is filled to the brim with gold and you’re going on vacation without engaging the deadlock. You would be practically asking thieves to come take whatever they want.
The scale of federal data exposure would be alarming any day, but the timing makes it even more suspect. These new vulnerabilities coincide with DOGE's sweeping campaign to centralize sensitive data1 from across the entire government, raising serious questions about how carefully—if at all—Americans' most personal information is being protected.
Every day, federal agencies collect and store your most sensitive information:
Social Security numbers
Medical histories
Bank account details
Tax records
And much more
Raise the Alarm–None of This is Normal for Government Networks
What this investigation uncovered raises serious alarm bells and reveals a level of risk to federal data that has little historic comparison. Not only is there a mass migration of government data happening at "move fast, break things" speed when any normal data migration would happen over the course of months or years, but even the most fundamental cybersecurity principles are being abandoned for convenience:
Database ports (like 1433, 3306, 5432) exposed directly to the internet for months, when not even a single day is advisable
This indicates that an admin actually had to change internal settings to be less secure, as these ports are protected by default
Weak authentication methods chosen over more secure options, potentially avoiding audit trails
Database servers replicating sensitive data in real-time for over 60 days—far beyond what any legitimate cloud migration requires
Security settings deliberately weakened—database ports are protected by default, meaning someone actually changed settings to be less secure
Ports are just what they sound like–”doors” that, when left open, can allow thieves to try to access the valuable stuff inside.
When database ports like 1433 (SQL Server), 3306 (MySQL), or 5432 (PostgreSQL) are directly exposed to the internet:
1. They become visible to automated scanning tools like Shodan, used by hackers and security professionals
2. They can face constant brute force attacks attempting to guess passwords
3. They're vulnerable to known exploits targeting specific database systems
4. Even without gaining full access, attackers can perform reconnaissance to plan more sophisticated attacks
I’ll break down exactly what I’m talking about below, but first let’s think about the impacts on you if the government fails to protect your personal data.
What's at risk if hackers breach government databases? Your life.
While my analysis uncovers an alarming and highly significant number of federal data systems exposed to cyberattacks, it’s tough to say exactly what’s inside without hacking it myself. But if we think about the data that DOGE has gained access to, the picture gets scary:
Your complete identity information (SSN, DOB, address history)
Tax and financial records, bank account numbers
Enrollment in specific government programs, benefits received
Medical and health information, veteran disability ratings
Identities of whistleblowers and domestic violence survivor
Employment history
Family member information
Think about a few scenarios that could play out if any or all of this data is sold to the highest bidder:
Health insurance companies could purchase leaked health data and use it secretly to deny life-saving medical care to patients.
Hackers could use your information to drain your bank account or take out loans in your name, and you would have to fight your bank to prove you weren’t responsible.
Trade secrets, even military technology, could be stolen by China to create low-cost knock-offs, causing companies to fold, workers to be laid off, and retirement funds to collapse.
Survivors of domestic violence might be stalked, harassed, or even murdered if their home addresses are leaked from HUD, which collects highly sensitive info related to housing discrimination claims.2
Russian ransomware gangs linked to state intelligence could use the vulnerabilities as an entry point to infiltrate and attack critical US energy, health, and telecommunications infrastructure. Consider a group like Black Basta3, who stole 5.6 million American patients’ data last year4 in a ransomware attack on Ascension Health.
Or one of the largest compromises5 in US history that happened late last year when Chinese intelligence6 breached 8 major US telecoms companies. If these highly sophisticated state actors get a foothold within federal systems, how much worse would it get?
What is Shodan?
This investigation relies entirely on open-source information from Shodan.io, essentially the Google of Internet-connected devices. Shodan continuously and actively scans the Internet, revealing insights into vulnerabilities and configurations of all sorts of devices. It’s used by security researchers and hackers alike–meaning anything that I’ve discovered through analysis, you can bet Russia and China know about it too.
We will focus on Microsoft’s Azure Gov Cloud, a specialized cloud hosting solution for the US federal government used by at least 15 major agencies7, including
Department of Agriculture
Department of Education
Department of Energy, National Nuclear Safety Administration
Department of Health and Human Services
Department of Housing and Urban Development
Department of Justice
Department of Labor
Department of State
Department of Transportation
Department of Veterans Affairs
Department of the Interior
Department of the Treasury
NASA
Small Business Administration (SBA)
United States Agency for International Development (USAID)
This list is to give you an idea of who Azure Gov Cloud’s customers are, and the type of data stored in general. I can’t tell you exactly what agency the databases we’ll talk about belong to, but the fact that Azure Gov Cloud is hosting it means they are either a federal agency or contractor. It’s also noteworthy that almost every single agency or department on this list has had its data systems accessed by Musk’s DOGE.
Major Finding #1: Government Database Systems Were Seen Over 2,000 Times This Year. With Risks Ranging from Moderate to Critical, Nearly All Significantly Above Historic Baseline
I actually uncovered so many observations of government database-related exposures that I need to break them down by product and level of risk. You don’t have to understand all the ins and outs to know that it’s not recommended or expected to expose any database infrastructure to the Internet, especially when you’re the US government.
I did my best to come up with legitimate explanations for why this level of data exposure is being seen now. While any individual data point (a server here or there) could have a reasonable explanation, I believe the sheer volume of security failures I’ve observed require further investigation–ideas include:
Current plaintiffs in lawsuits challenging DOGE's access8 to federal data–especially9 New Mexico et al. v. Musk–could use my report as a roadmap for filing targeted discovery motions or subpoenas
Congressional hearings and investigations to obtain access audit logs and chain of custody
Inspector General audits to evaluate agency compliance with FISMA, FedRAMP, and OMB Circular No. A-13010
Imagine a government building containing our nation's most sensitive files.
Normally, a security guard (firewall) controls access, and each room has sophisticated locks. Now, the guard has been fired, and someone replaced the high-security locks with dollar-store versions. Even worse, they've posted the building's address online.
This is essentially what's happening with hundreds of government database servers exposed over the last three months.
In this metaphor:
The government building is a server with an IP address.
Each room is a port associated with a different database system.
And actually, someone had to go to the dollar store and uninstall the good locks to replace them with cheap ones. What am I referring to?
Azure Government Cloud, by default, has plenty of state-of-the-art security tools in place. Someone (whoever was making these changes on the inside) had to actually change the default settings to be less secure.
The sheer volume of exposed government database systems I've documented is deeply alarming, not just to me but to several cybersecurity professionals more experienced than myself.
To help understand the scope and severity, I've categorized these exposures by risk level:
a. Moderate Risk: Over 150 Government Database Servers Were Seen More than 2,000 Times
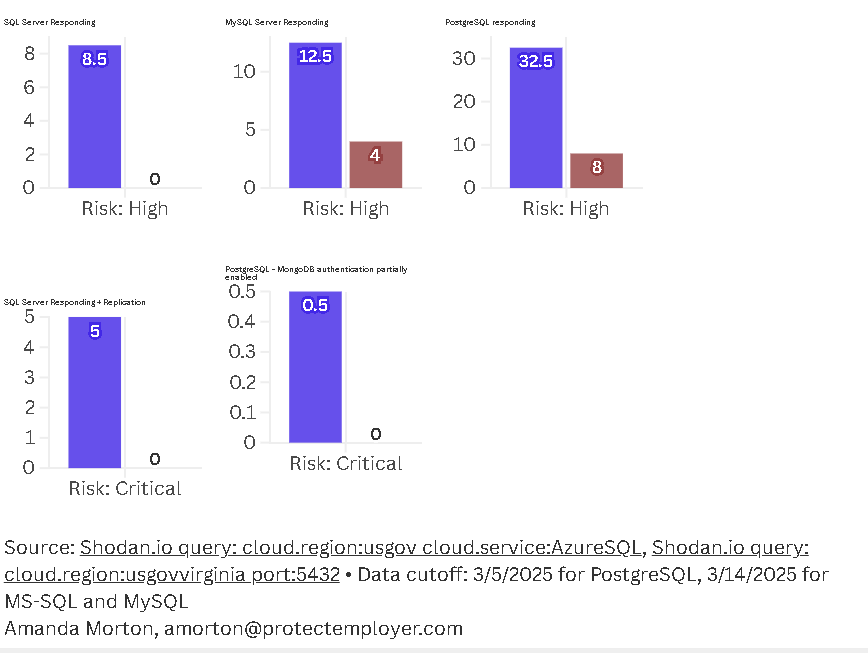
Between January and March of this year, over 150 database servers were observed exposed to the Internet more than 2,000 times.1112 (Date sources13, 14) While exposing database endpoints is never recommended, this is the biggest “bucket” of observations, to which I would assign moderate risk.
Such repeated exposures certainly make these servers an interesting target for foreign intelligence or just normal cybercriminals.
b. High Risk - Government Database Servers Responded to Connection Attempts More than 800 Times
From the above group, government database servers responded to connection attempts 655 times15, leaving sensitive systems vulnerable to a variety of attacks. If attackers gain access to one server, they can steal the data or even use SQL injection to change or delete records. Even worse, the responses indicate that a less secure authentication method (simple username and password via SQL authentication) is being used.
This is another example of the government administrator who made these changes deliberately choosing less secure options than is available to them–a more secure (and obvious) choice would be to use Azure’s own authentication method, which relies on tokens that expire and are linked to specific Azure Gov Cloud accounts. Further, all of these database services are blocked by Azure Cloud by default, meaning the administrator manually changed network settings to expose these ports.
This part has me curious–is there some reason to not use Azure authentication?
The only one that leaps to mind is that someone wants people who don’t have Azure Gov accounts to be able to access these databases.
c. Critical Risk - Immediate Action Required
Among the initial 2,400+ observations, over 200 of them are linked with data replication (port 5022) and show responses to connection attempts, meaning that a significant number of government database servers are not only exposed but are actively replicating data across systems in real-time.
The servers with an open replication port began responding to connection attempts starting on March 7 and continued through my data cutoff March 14, 2025.
Think of replication as copying data from one server to another. This can be useful during a routine migration to the cloud for a brief period, and then the “door” is closed again.
These servers have been live-updating copies of themselves for a week. This situation presents a critical risk for several reasons:
Live Data in Transit: These connections carry actual government data in real-time as it moves between systems
Privileged Access: Replication channels typically use highly-privileged database accounts with extensive permissions, making them a high-value target
Backdoor Entry and Lateral Movement: An attacker who compromises a replication channel might be able to:
Intercept sensitive data as it's being copied
Potentially inject malicious data into the replication stream
Gain administrative-level access to connected database systems
Industry standard practice limits replication exposure to hours or days at most, with strict security controls. The weeklong exposure observed here violates fundamental security principles and compliance requirements like FISMA and NIST 800-53.
The fact that US government-affiliated endpoints were observed using database replication over 200 times in March indicates this isn't an isolated issue but a systemic security risk across multiple government systems
Major Finding #2 - 54 Newly-Created or Previously-Internal Government Database Endpoints Responded to Connection Attempts 352 Times
This investigation identified 54 unique database endpoints with no DNS records, indicating they are either newly created or were previously only seen on internal government networks.
Why is this bad?
These servers shouldn't be visible at all. If this is part of some sort of migration to the cloud, it’s being handled in shockingly insecure fashion.
They remained exposed for 48 consecutive days This isn't a brief exposure during maintenance—it's a persistent vulnerability spanning nearly two months.
Each newly discovered database endpoint is linked to a known one via their SSL (security) certificate. This puts out a giant “hack me!” sign for threat actors.16
Major Finding #3 - Potential DoD Supply Chain Asset Compromised by Botnet with Nodes in China, Russia, and Iran
A Polish software company, Kruko.io, with connections to the U.S. Department of Defense supply chain, has had their Azure Government Cloud infrastructure compromised and included in a global botnet with nodes in Russia,17
This appears to stem from an unsecured Redis database instance.
Redis Vulnerability Explained
Redis is a NoSQL database that enhances the speed of database queries through caching.
If the Redis instance is not properly secured with password authentication, it can be taken over by malicious actors. Once compromised, these instances can be used as nodes in a botnet to replicate and spread malware.
Brief timeline of the attack
March 9 - Kruko's Redis instance was identified as a "slave" of a Chinese IP address 47[.]236[.]197[.]48, meaning it was one of many nodes around the world pushing commands and possibly data back to the Chinese server.
March 10 - Kruko’s Redis node became a "master," continuing to replicate a key-value store identified as malicious by Shodan.
March 17 - Kruko’s Redis is once again a slave of Chinese IP address 47[.]236[.]197[.]48
March 18 - At time of writing, Kruko’s Redis is now a slave of evil.com
Kruko is likely a victim of a security misconfiguration, so I won’t cite their IP address in hopes they will take steps to fix this soon.
Kruko, if you’re reading this, please secure Redis immediately!
Connection to the Department of Defense Supply Chain
Kruko.io appears to be part of the Department of Defense supply chain through the following relationships:
Kruko → Couchbase → Applied Research Associates, Inc. → Department of Defense
Kruko is a development partner for Couchbase starting around July 202418
Couchbase is a subcontractor to Applied Research Associates19 (ARA) starting July 2024, supplying IT services for ARA’s contract20
ARA was awarded a $550 million Department of Defense contract in 2020.
Azure Government Cloud requires verification that users are either:
U.S. government entities
Authorized contractors working with the U.S. government
This confirms Kruko likely has a legitimate connection to U.S. government projects.
Kruko developed AI integration capabilities for Couchbase's Capella platform, creating "Capella iQ" - an AI assistant that:
Allows database queries to be written in natural language
Provides real-time code suggestions and optimizations
Automates repetitive database tasks
It’s highly possible that Kruko’s technology is incorporated into solutions being provided to the Department of Defense through the Couchbase-ARA contract. Urgent action must be taken to remediate this security compromise immediately.
So, how far above historic baseline is all this?
You might be thinking, "Okay, maybe all this is normal." Let’s take a look at the historical baseline for comparison.
Up until now, I’ve mainly focused on the number of observations—how Shodan, which actively scans the entire internet, identifies a particular IP address. It's important to note that the same IP address can be observed multiple times if it has services that respond to the scanner.
To analyze trends over time, we need to focus on the number of unique IP addresses observed each month.
Using the same risk categories (moderate, high, critical) and product types from above, I will show you how many unique IP addresses we’ve seen since January compared to the historical maximum from the previous 3 to 4 years.
Key takeaways:
Current database exposure levels significantly exceed historical maximums across nearly all categories.
PostgreSQL servers responding to external connections have increased 4x over previous maximums, creating substantial risk.
Several critical-risk configurations have appeared that were previously non-existent in our historical data.
Open MySQL ports have jumped from a previous maximum of 3 to 43 per month, a 14x increase.
Data sources: Shodan Trends21,22 and Shodan Search (ibid)
Urgent Action Needed
Your personal information could be at risk right now. Contact your representatives, file FOIA requests (template here), and demand answers from federal agencies. The government has a legal obligation to protect your data—and right now, they're failing that obligation.
This isn't about politics. This is about protecting every American's privacy and security in an increasingly digital world.
Methods
Data collection began on February 22, 2025, and ended on March 5, 2025 for PostgreSQL endpoints (port 5432) and March 14, 2025 for MS-SQL Server (port 1433) and MySQL (port 3306).
All data was downloaded either through querying Shodan.io’s front-end, or using Shodan’s API to call “timeline” data from the previous 90 days. For historic comparisons, I used Shodan Trends (trends.shodan.io) Because there are substantially more search filters available using Shodan Search compared to Shodan Trends, I had to get creative with queries to get historic results.
For example, on Shodan Search I am able to search
cloud.region:usgov cloud.service:AzureSQL
But in order to pull up the same results in Shodan Trends, I have to search
asn:AS8070 hostname:database.usgovcloudapi.net
asn:AS8075 hostname:database.usgovcloudapi.net
Because Shodan Trends only returns counts of unique IP addresses/devices per month, I only used unique IP addresses from the current dataset for historical baseline comparisons.
From there, I analyzed the data in Excel, filtering by ports 1433 (MS-SQL Server), 3306 (MySQL), 5432 (PostgreSQL), and 5022 (common for SQL replication), and used pivot tables to count numbers of observations per day and month, as well as unique IP addresses. I filtered by HTTP header response to identify SQL database endpoints that responded to Shodan’s connection attempts.
The moderate risk category includes all observations of Azure Gov Cloud IPs with SQL-related ports open. The high risk category uses a filter on the HTTP response data to identify successful responses to Shodan’s connection attempts. The critical category is filtered further to only include successful HTTP responses and port 5022 open.
I used Security Trails to run DNS queries on all PostgreSQL endpoints to identify the 54 newly-created or newly-exposed endpoints with no DNS records. Each of those 54 endpoints listed at least one known database endpoint with DNS records as the Subject Alternative Name in the SSL certificate.
The network of Redis “slaves” associated with Chinese master IP address was identified by using the query “master_host:47[.]120[.]58[.]144” and I used IPinfo.io to create a global map.
Throughout this investigation, I have taken care to handle sensitive data responsibly and to avoid disclosing specific IP addresses that could lead to further exploitation.
If you are a cybersecurity researcher, I will be happy to provide you with additional data on request.
Works Cited
Kelly M. Elon Musk Ally Tells Staff “AI-First” Is the Future of Key Government Agency [Internet]. WIRED. 2025 [cited 2025 Mar 17]. Available from: https://www.wired.com/story/elon-musk-lieutenant-gsa-ai-agency/
Coburn J. DOGE Gains Access to Confidential Records on Housing Discrimination, Medical Details — Even Domestic Violence [Internet]. ProPublica. 2025 [cited 2025 Mar 17]. Available from: https://www.propublica.org/article/doge-elon-musk-hud-housing-discrimination-privacy-domestic-violence
Goodin D. Black Basta ransomware group is imperiling critical infrastructure, groups warn [Internet]. Ars Technica. 2024 [cited 2025 Mar 17]. Available from: https://arstechnica.com/security/2024/05/black-basta-ransomware-group-is-imperiling-critical-infrastructure-groups-warn/
Alder S. Ascension Ransomware Attack Affects 5.6 Million Patients [Internet]. The HIPAA Journal. 2024 [cited 2025 Mar 17]. Available from: https://www.hipaajournal.com/ascension-cyberattack-2024/
Mitchell A, Moeder N. Sweeping Chinese hack of U.S. telecoms firms is “still going on,” homeland security secretary says [Internet]. NBC News. 2024 [cited 2025 Mar 17]. Available from: https://www.nbcnews.com/politics/national-security/vast-chinese-hack-eight-us-telecoms-firms-still-going-official-says-rcna181319
Rob Freeman. Why Is China Hacking U.S. Telecommunications Infrastructure? | Rob Freeman [Internet]. Rob Freeman. 2024 [cited 2025 Mar 17]. Available from: https://robfreeman.com/why-is-china-hacking-u-s-telecommunications-infrastructure/
FedRAMP Marketplace - Azure Gov Cloud [Internet]. FedRAMP.gov. 2025. Available from: https://marketplace.fedramp.gov/products/F1603087869
Just Security. Litigation Tracker: Legal Challenges to Trump Administration Actions [Internet]. Just Security. 2025 [cited 2025 Mar 18]. Available from: https://www.justsecurity.org/107087/tracker-litigation-legal-challenges-trump-administration/
Chutkan JTS. Judge Order for Expedited Discovery in New Mexico, et al. v. Elon Musk, et al. [Internet]. Documentcloud.org. 2025 [cited 2025 Mar 18]. Available from: https://www.documentcloud.org/documents/25559976-nmmuskdiscord031225/
CIRCULAR NO. A-130 TO THE HEADS OF EXECUTIVE DEPARTMENTS AND AGENCIES SUBJECT: Managing Information as a Strategic Resource [Internet]. Office of Management and Budget, White House; Available from: https://www.whitehouse.gov/wp-content/uploads/legacy_drupal_files/omb/circulars/A130/a130revised.pdf
Morton A. Moderate risk - Government database servers on Azure Gov Cloud observed 2,444 times Jan-March 2025 [Internet]. Flourish. 2025 [cited 2025 Mar 18]. Available from: https://public.flourish.studio/visualisation/22165149/
Morton A. Risk ratings for Azure Gov Cloud exposed database servers, Jan - March 2025, column chart with filter [Internet]. Flourish. 2025 [cited 2025 Mar 18]. Available from: https://public.flourish.studio/visualisation/22178169/
Shodan Search query: cloud.region:“usgov” cloud.service:“AzureSQL” [Internet]. Shodan.io. 2025 [cited 2025 Mar 17]. Available from: https://www.shodan.io/search?query=cloud.region%3A%22usgov%22+cloud.service%3A%22AzureSQL%22
Shodan Search query: cloud.region:usgovvirginia port:5432 [Internet]. Shodan.io. 2025 [cited 2025 Mar 18]. Available from: https://www.shodan.io/search?query=cloud.region%3Ausgovvirginia+port%3A5432
Morton A. Risk matrix for Azure Gov Cloud exposed database servers [Internet]. Flourish. 2025 [cited 2025 Mar 19]. Available from: https://public.flourish.studio/visualisation/22165407/
Morton A. 54 Newly-Discovered Azure Gov Cloud PostgreSQL endpoints allowed 321 Connection Attempts Jan-March 2025 [Internet]. Flourish. 2025 [cited 2025 Mar 19]. Available from: https://public.flourish.studio/visualisation/22181910/
Morton A. IP Map Report of Redis Slave Nodes Linked to Chinese IP address 47[.]236[.]197[.]48 [Internet]. Ipinfo.io. 2025 [cited 2025 Mar 18]. Available from: https://ipinfo.io/tools/map/cfd73c2e-b94e-4075-8a5c-aa1e75d7f4eb
Couchbase Capella: Revolutionizing Cloud Database Management | Kruko [Internet]. Kruko.io. 2024 [cited 2025 Mar 18]. Available from: https://web.archive.org/web/20240713212845/https://www.kruko.io/case-studies/couchbase
USAspending.gov - Couchbase Federal Sub-Contract Awarded July 2024 [Internet]. Usaspending.gov. 2025 [cited 2025 Mar 18]. Filter by Sub-awards. Available from: https://www.usaspending.gov/search/?hash=e59f387b5a9939f0dfb9e884c175a79f
USAspending.gov - Department of Defense Contract Award to Applied Research Associates PIID 47QFCA20F0022 Current Award Amount $554.3 Million. See sub-award history for Couchbase. https://www.usaspending.gov/award/CONT_AWD_47QFCA20F0022_4732_GS00Q14OADU304_4732
Shodan Trends query: asn:as8070 hostname:webqueryendpoint.database.usgovcloudapi.net [Internet]. Shodan. 2025 [cited 2025 Mar 20]. Available from: https://trends.shodan.io/search?query=asn%3Aas8070+hostname%3Awebqueryendpoint.database.usgovcloudapi.net#overview
Shodan Trends query asn:as8075 hostname:webqueryendpoint.database.usgovcloudapi.net [Internet]. Shodan. 2025 [cited 2025 Mar 20]. Available from: https://trends.shodan.io/search?query=asn%3Aas8075+hostname%3Awebqueryendpoint.database.usgovcloudapi.net#overview

















This has to be done on purpose just to expose our data, allow our enemies to take it. That has to be the story. There's no other explanation. No government agency would ever do this.
I believe you meant to write "2025" in Key Finding #1...