Ukraine’s Drone Revolution and the Lethal Convergence of Cyber-Kinetic War
With GPS spoofing and real-time cellular tracking in play, cyber tools have evolved from auxiliary roles to critical instruments of war, and there's no going back.
Ukraine’s Drone Revolution and the Lethal Convergence of Cyber-Kinetic War
This analysis argues that the 2022 Russian invasion of Ukraine signaled a convergence between the domains of cyber and kinetic warfare, defying the previous consensus that cyber-warfare has little impact on or relationship with physical conditions on the battlefield.
Cyber-enabled attacks have crossed the threshold of lethality and instrumentality, with the ability to deliver decisive victory or punishing defeat on the battlefield. In a theater of war defined by drones, cyber-attacks can be used to foil enemy attacks, disrupt tactical communications, and create opportunities for soldiers to advance.
Conversely, failure to enact a robust cyber-defense can have deadly consequences.
This article draws from Air University’s Michael P. Kreuzer's view that cyber warfare is better conceptualized as a multi-domain operational construct rather than a discrete domain such as land, sea, air, and space. We consider electromagnetic attacks to bridge the gap between physical and digital warfare, yet remain firmly within the realm of cyber operations.
The Evolution of Cyber Warfare in Ukraine, 2000-2016
Thomas Rid’s 2011 paper, Cyber War Will Not Take Place, argued that cyberattacks lacked the lethality, instrumentality, and political significance to be classified as war. While this assessment was valid then, the unprecedented use of drones in tandem with cyber operations in the Russia-Ukraine war has revolutionized conflict.
Drones themselves are kinetic instruments, yet they rely on GPS for navigation, cellular networks for commands, and AI for enhanced targeting, all of which are vulnerable to cyber exploitation.
A 2019 study comparing cyber and kinetic operations during the 2014 Crimea invasion found weak coordination, likening it to airpower’s infancy during WWI. However, just as a military paradigm shift helped airpower evolve into a strategic force during WWII, cyber warfare is maturing into an offensive force multiplier capable of chaos and destruction on the battlefield.
History repeats itself as the new airpower revolution—drone warfare—ushers in a chapter of lethal, instrumental, and politically-driven cyber warfare. And in turn, as weapons systems become more technologically advanced, they become more vulnerable to electronic attacks.
Close, but not quite: Cyber War between Russia and Ukraine in 2022
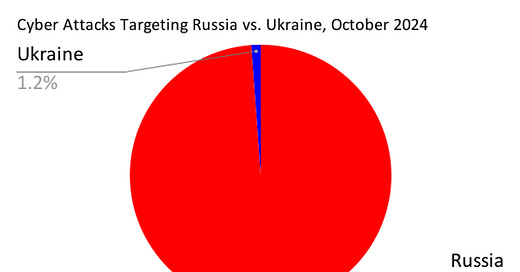
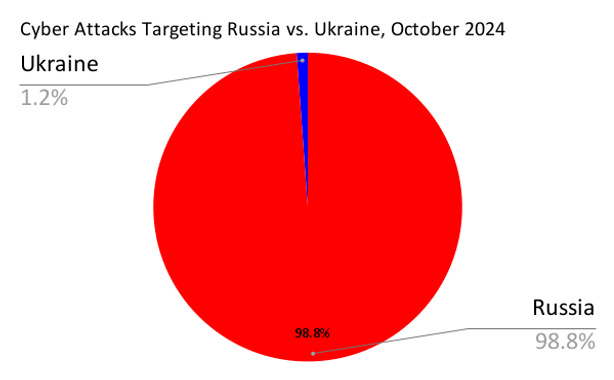
After Russia’s invasion of Ukraine in 2022, Russian cyber attacks largely focused on disrupting but not destroying Ukraine’s military and civilian infrastructure, and degrading morale with information operations. Russia's 2022 cyber attacks, despite increasing by 75% post-invasion, failed to achieve decisive strategic gains, likely due to Ukraine’s resilient cyber defense and strong international support. By 2024, Russia has become a top target of global cyberattacks, facing nearly 99% of all documented incidents compared to Ukraine.
Ukraine’s 2023 Drone Revolution Marks Cyber’s Convergence with Kinetic War
So far, the evidence does not suggest that cyber strategies have been decisive in the Russia-Ukraine war.
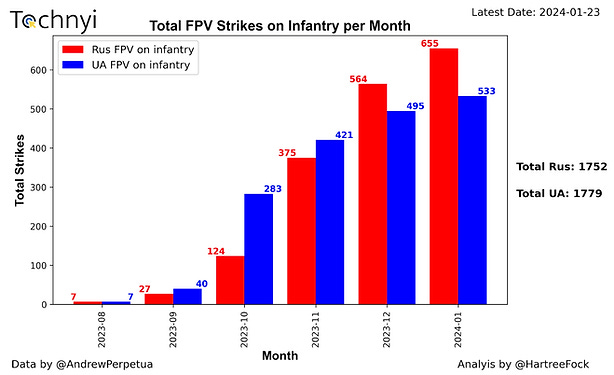
However, 2023 marked a turning point as Ukraine escalated its drone strikes during a renewed counteroffensive against Russian gains.
Between September 2023 and January 2024, both Ukraine and Russia significantly increased their use of drones in combat, with Ukraine maintaining a clear but gradually narrowing advantage.
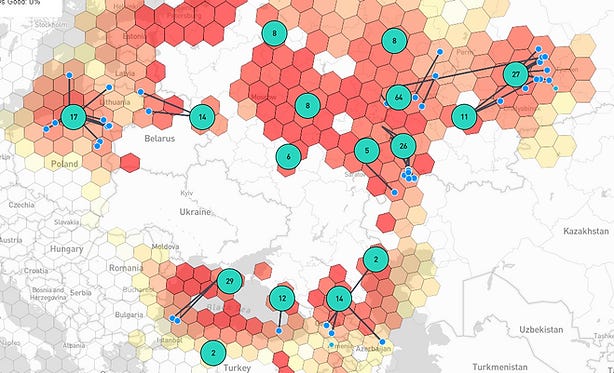
Moscow, meanwhile, effectively deployed “suicide drones” to target Ukraine’s critical infrastructure and even civilian shelters, causing widespread damage.
In response to Ukraine’s intensified drone campaign, Russia opened a dangerous new cyber front by dramatically increasing GPS spoofing attacks to disrupt Ukrainian drone operations.
Aviation experts noted a 400% increase in GPS spoofing attacks worldwide between September 2023 and July 2024, identifying Russia as a major hotspot. These attacks, which broadcast false coordinates to mislead GPS navigation, have not only hindered Ukraine’s drone capabilities but also raised serious safety concerns for civilian aircraft operating in the region.
Russia’s GPS offensive caused Ukraine’s target strike rate to plummet to as low as 10% for new pilots, compared to 80% for experienced operators prior to the spoofing campaign.
At the same time, both sides are weaponizing cellular networks to track soldiers and bomb enemy positions in real-time. Using cyber operations to accomplish targeting, a task previously performed by human intelligence, represents an evolution of cyber’s instrumentality.
Taken together, these trends demonstrate that cyber operations have transcended their previous auxiliary role to become a decisive force on the physical battlefield.
The Future of Cyber-Kinetic Warfare
The war in Ukraine demonstrates that cyber warfare has crossed the Rubicon into lethal and instrumental territory through the emergence of hybrid cyber-kinetic warfare. From GPS spoofing attacks on drones to weaponizing cellular networks for real-time targeting of enemies, the conflict illustrates how cyber and kinetic strategies have become more deeply integrated than ever before. This inflection point signifies not merely a tactical shift but a fundamental redefinition of warfare's future.
As we navigate this new era of cyber-kinetic hybrid warfare, the implications for both U.S. allies and adversaries are striking. For allies, the invasion has catalyzed increased cyber militarization and collaboration, demonstrated by NATO’s enhanced cyber defense posture and new partnerships between the UK, U.S. and Japan.
Russia has made significant advancements in cyber warfare by leveraging increasingly sophisticated tactics to achieve strategic goals. Beyond traditional cyber espionage and attacks on critical infrastructure, Russia has developed offensive capabilities like GPS spoofing to enable sweeping disruptions of adversary operations.
Russia continues to blur the lines between combatants and non-combatants by blending cyber, psychological, and kinetic attacks to degrade civilian infrastructure alongside its adversary’s combat readiness and morale.
Further, non-state actors are empowered by the availability of off-the-shelf technology such as drones and Ransomware-as-a-Service to act as a force multiplier in asymmetric conflict. The difficulty in attributing cyber attacks lends non-state actors plausible deniability and shields them from the threat of retaliation.
In the fog of cyber-kinetic war, non-state actors stand to enhance their operational reach using low-cost cyberattacks on civilian infrastructure while eluding accountability.
Just as airpower revolutionized 20th-century conflict, the rise of cyber warfare is transforming the very nature of modern combat.
Yet, the accessibility of cyber operations to state and non-state actors alike creates a far more complex and unpredictable battlefield. As nations increasingly deploy emerging technologies on the battlefield, their vulnerabilities multiply, making cyber defense and offense as critical as conventional military force. The Ukraine war demonstrates that cyber strategies are no longer mere support tools—they are decisive weapons in the future of war.
Works Cited
Devine, K. (2023, January 4). Ukraine war: Mobile networks being weaponised to target troops on both sides of conflict. Sky News. https://news.sky.com/story/ukraine-war-mobile-networks-being-weaponised-to-target-troops-on-both-sides-of-conflict-12577595
Hashimoto, T. (2024). Operationalizing Japan-U.S. Cooperation on Critical Infrastructure Cybersecurity and Resilience. https://www.csis.org/analysis/operationalizing-japan-us-cooperation-critical-infrastructure-cybersecurity-and-resilience
Hunder, M. (2024, October 31). Ukraine rolls out dozens of AI systems to help its drones hit targets. Reuters. https://www.reuters.com/world/europe/ukraine-rolls-out-dozens-ai-systems-help-its-drones-hit-targets-2024-10-31/
Kaspersky Labs. (n.d.). STATISTICS | Kaspersky Cyberthreat live map. STATISTICS | Kaspersky Cyberthreat Live Map. Retrieved November 13, 2024, from https://cybermap.kaspersky.com/stats
Kostyuk, N., & Zhukov, Y. M. (2019). Invisible Digital Front: Can Cyber Attacks Shape Battlefield Events? The Journal of Conflict Resolution, 63(2), 317–347. https://www.jstor.org/stable/48596899
Kreuzer, M. P. (2021, July 8). Cyberspace is an Analogy, Not a Domain: Rethinking Domains and Layers of Warfare for the Information Age. The Strategy Bridge. https://thestrategybridge.org/the-bridge/2021/7/8/cyberspace-is-an-analogy-not-a-domain-rethinking-domains-and-layers-of-warfare-for-the-information-age
Kunertova, D., & Herzog, S. (2024). Emerging and Disruptive Technologies Transform, but Do Not Lift, the Fog of War – Evidence from Russia’s War on Ukraine [Application/pdf]. https://doi.org/10.3929/ETHZ-B-000696795
Live GPS Spoofing and Jamming Tracker Map. (n.d.). Retrieved November 7, 2024, from
https://www.spoofing.skai-data-services.com/
Mueller, G. B., Jensen, B., Valeriano, B., Maness, R. C., & Macias, J. M. (2023). Cyber Operations during the Russo-Ukrainian War. https://www.csis.org/analysis/cyber-operations-during-russo-ukrainian-war
NATO. (2024, July 30). Cyber defence. NATO. https://www.nato.int/cps/en/natohq/topics_78170.htm
OPSGROUP. (2024, July 17). 400% increase in GPS Spoofing; Workgroup established – International Ops 2024 – OPSGROUP. https://ops.group/blog/400-increase-in-gps-spoofing-workgroup-established/
Rid, T. (2012). Cyber War Will Not Take Place. Journal of Strategic Studies, 35(1), 5–32. https://doi.org/10.1080/01402390.2011.608939
UK Cabinet Office. (2024, January 17). UK Government strengthens UK-Japan partnership on cyber. GOV.UK. https://www.gov.uk/government/news/uk-government-strengthens-uk-japan-partnership-on-cyber