I Mapped the Global Network Big Balls is Probably Using to Sell Your Data
My months-long investigation of Edward “Big Balls” Coristine shows that his company, Packetware, operates a global server network with capabilities befitting a large-scale data smugg
My months-long investigation of Edward “Big Balls” Coristine shows that his company, Packetware, operates a global server network with capabilities and usage metrics befitting a large-scale data smuggling operation, not a simple web hosting company as he claims. Since February, I observed traffic patterns and security settings that appear designed to let co-conspirators extract data from anywhere on the planet. In fact, Packetware’s network security is worse than an average home Wi-Fi system. Foreign intelligence agencies, criminals, or anyone online can intercept or dump data at will.
Packetware's poor cybersecurity allowed me to directly inspect the network's metrics. At the height of DOGE activity in February 2025, the network sent 150% more data than it received, sending over 32,000 gigabytes from the U.S. through a labyrinth of virtual machines around the world in just half a day. Since the peak in February, the amount of traffic has slowed to a relative trickle. But as of publication, Big Balls' network sends out 26 times as much as it takes in.
If Packetware was a niche private web hosting company, as Big Balls claims, then we would see a modest trickle of relatively balanced traffic. The traffic patterns are far more indicative of how ransomware gangs move stolen secrets while destroying the trail of evidence behind them.
With extremely high bandwidth and a series of proxies that can hide the flow of traffic, Packetware has the capacity to deliver our nation's most tightly-held secrets all over the world. If Big Balls is indeed smuggling large volumes of American federal data, the network's deliberate lack of cybersecurity opens the door for China, Russia, or any foreign adversary to access our most sensitive national security information.
Critically dangerous settings include:
No passwords or authentication needed to explore the entire network
Logs deleted every 12 hours, compared to the weeks-long retention of normal monitoring systems
Configuration that permits unlimited data extraction by any user
The network exhibits classic indicators normally associated with malware gangs stealing data/mass data exfiltration/stealing data: 26 times more data flowing out than coming in, servers spread across five countries to mask data trails, and open-access security that requires no credentials. Due to DOGE's constant destruction of evidence, this may be the closest to a smoking gun we'll ever get that America’s most sensitive intelligence is being systematically funneled overseas.
Edward "Big Balls" Coristine: The Russian Hacker Connection at the Heart of DOGE
Edward "Big Balls" Coristine is a 19-year-old programmer who has played a significant role in Trump's second term as president. He was first employed at the Department of Government Efficiency, then the General Services Administration, and finally at the Social Security Administration, in each case given broad access to federal digital systems. Trump's takeover of the Washington DC police department and deployment of the National Guard in DC were a direct response to a group of teenagers allegedly assaulting Big Balls.
In 2022, when he was in high school, Big Balls created Packetware. Until 2024, Packetware provided web hosting designed to evade law enforcement. His customers were Russian hackers who bragged about selling stolen data and cyberstalking an FBI agent.
Big Balls met his hacker buddies through "the Com," a loose online network that bridges North American and Russian cybercriminals with a reputation for doxxing, swatting, and extorting both victims and fellow hackers alike. Cybersecurity expert Brian Krebs calls the Com the "English-language cybercriminal hacking equivalent of a violent street gang."
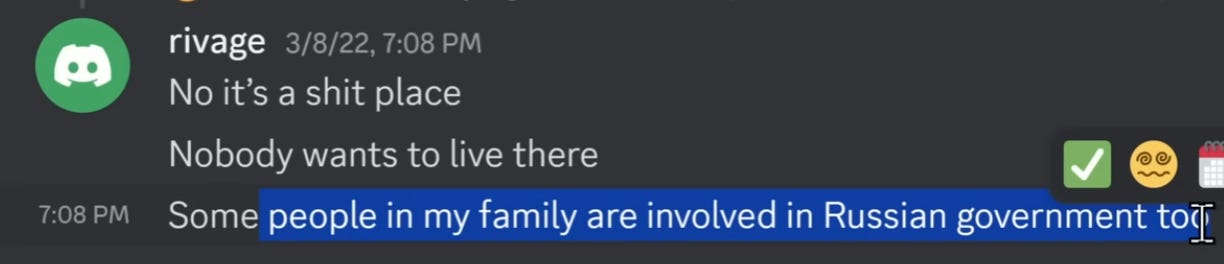
On Discord, Big Balls complained that "I don’t think there’s a lot of money to be made in the com".
YouTuber No Text To Speech discovered Discord messages where Big Balls (username: rivage) admitted to having family members in the Russian government.
Big Balls was fired from Path Network for leaking company secrets and moved directly to interning at Neuralink in summer 2024. Until July 2024, just months before becoming Musk's right-hand man at DOGE, Big Balls was still hosting malware sites spreading viruses across the internet.
To summarize, Trump and Musk gave the highest level security clearance and broad access to all Americans' sensitive federal data to a teenager with family in the Russian government and a history of leaking company secrets, supporting anti-American hackers, and spreading computer viruses.
Big Balls' Network Transferred Terabytes of Data During the Height of DOGE
Packetware claims to be a small Virtual Private Server hosting provider, but its traffic patterns tell a different story.
VPS hosting typically generates balanced traffic patterns as customers pull content from servers. Instead, Packetware runs a secretive network that processes amounts of data on par with Silicon Valley firms.
Big Balls' small-time hosting company boasts a rather inactive Discord channel with roughly 70 members, most of whom seem to show just casual interest instead of being actual paying customers.
Yet for such a tiny company, Packetware's outbound data flows are absolutely stratospheric.
Digital Air Traffic Control for Stolen Data
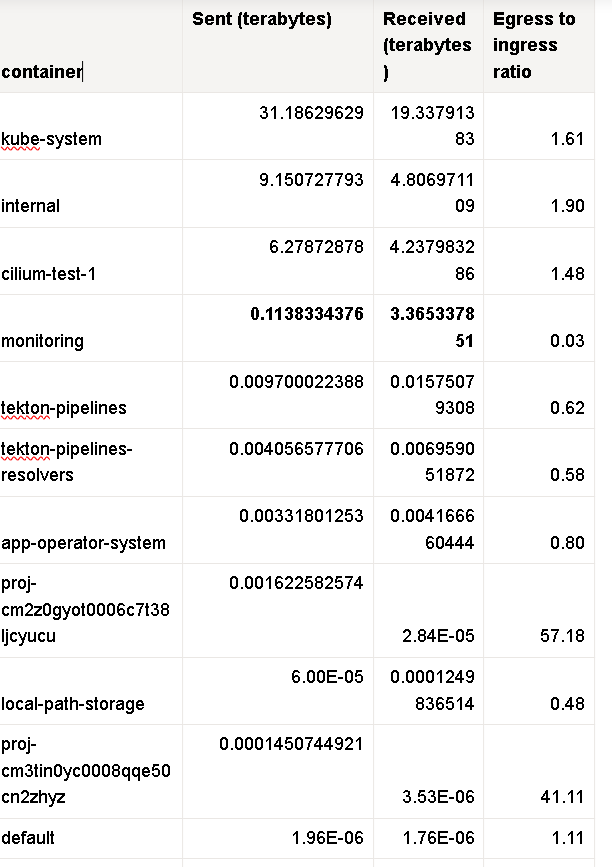
In February, I discovered Packetware's digital equivalent of an air traffic control tower hosted in Montreal. (Original spreadsheet here.) This server runs monitoring software that tracks network traffic from nodes worldwide. However, the overwhelming trend is data going out to destinations obscured by the layers of constantly changing proxies. The traffic patterns align precisely with how state-sponsored cyber threat groups move stolen information from victims to servers under their direct control.
February 6, 2025
Total Received: 32,542 GB (31.78 TB) over 12 hours
Total Sent: 47,872 GB (46.75 TB) over 12 hours
Net Flow: ~15 TB outbound
Ratio: ~1.5 TB out for every 1 TB in
Combined Traffic Volume: 78.52 TB
To put this in perspective: if you printed the data entering the network on February 6th, it would create a stack of 839,000 encyclopedias measuring 26 miles tall. The outbound data would reach 46.6 miles into the stratosphere.
In this exact same time frame, Big Balls' Packetware network hosted around 60 remote servers in Germany. These 60 German servers almost certainly formed the backbone of a massive exfiltration network as part of the largest data heist in history. We can only assume that any data DOGE accessed, especially at the height of operations in February 2025, is now in the hands of America's enemies.
Since the height of DOGE activity, the overall amount of data leaving Big Balls' network has slowed significantly, but the proportion of data going out vs coming in has skyrocketed--with 26 times more going out than coming in.
September 3, 2025
Total Received: ~15.75 GB per 12 hours
Total Sent: ~411.4 GB
Net Flow: 427.15
Ratio: 26 GB out for every 1 GB in
Big Balls' Network Design Is Perfect for International Data Smuggling
Packetware's system provides ideal infrastructure for covertly sending government data overseas:
Servers spread across multiple countries (US, Canada, Netherlands)
Dangerous security settings allowing anyone to map network without authentication
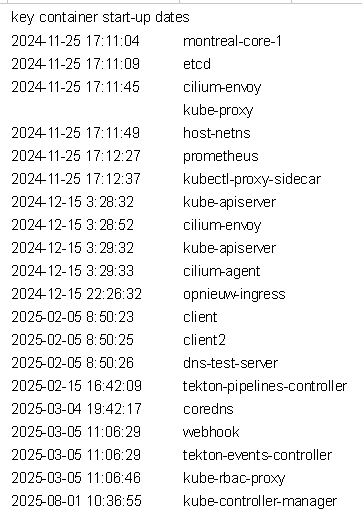
Logs deleted every 12 hours (except we can see the date when containers first started)
Constant creation and destruction of containers, destroying all evidence
26:1 outbound traffic bias (opposite of normal web hosting)
How the Data Smuggling Operation Works
Based on network analysis, here's how the operation likely functions:
Insider Access - DOGE personnel access federal networks using their unlimited privileges
Initial Transfer - Data moves from government systems to U.S.-based proxy nodes
Global Proxies - Information travels through multiple international proxy servers (Montreal, Amsterdam, Dallas, Los Angeles) to obscure its origin
Final Delivery - Data arrives at remote SSH servers in Europe, completely untraceable
The sophisticated routing makes detection nearly impossible while providing plausible deniability for any intercepted communications.
Government Officials and Security Experts Already Warned DOGE Is Damaging National Security
Security experts and even the government's own lawyers warned that allowing DOGE staff unchecked access to sensitive federal systems without required security clearances is a grave threat to national security. DOGE has never explained why such sweeping access to the Treasury's payment systems or even nuclear secrets is needed for a routine audit.
More recently, the highest-ranking data official at the Social Security Administration, Charles Borges, blew the whistle on DOGE's most dangerous operation yet. Borges served his country for over 20 years as a Navy veteran with deployments to Afghanistan before joining the public sector. He watched in horror as DOGE seized control of the database containing every single American's Social Security number with no oversight.
In his complaint, Borges warned:
"If malicious actors gain access to this cloud environment, Americans may be vulnerable to widespread identity theft, may lose crucial health and food benefits, and the government might have to issue new Social Security numbers to every American at significant expense," Borges warned in his whistleblower complaint.
The SSA whistleblower revelation aligns with an earlier disclosure by an IT worker at the National Labor Relations Board, where DOGE allegedly stole 10 gigabytes of sensitive labor data. Within minutes of DOGE accessing NLRB systems, someone with a Russian IP address began attempting to log in using DOGE's newly created username and password.
The "DOGE Approach" to Data Theft
America's most respected cybersecurity expert just warned Congress that DOGE has "created unprecedented cybersecurity risks for the American people and government. Bruce Schneier's testimony reveals DOGE's systematic "four pillar approach" that violates every fundamental principle of cybersecurity:
1) Consolidate all citizen data into one massive target
Instead of keeping Social Security records separate from tax data, separate from health records, DOGE is combining everything into one giant database. Think of it like moving all your valuables from separate safe deposit boxes into one massive vault that dozens of people can access. The SSA whistleblower confirms DOGE seized control of every American's Social Security information. Court records show they accessed Treasury payment systems processing trillions in government transactions. DOGE is also working to target immigrants using their IRS and Social Security information--data that can only be collected by immigrants who work and pay taxes. The data of over 300 million Americans was copied to an insecure cloud server, risking widespread identity theft, loss of essential benefits, and illicit Treasury access. In the worst case, bad actors could halt, reroute, or alter trillions of dollars in federal payments, disrupting Social Security, Medicare, tax refunds, and salaries. This would cause financial chaos for millions of Americans, halt all delivery of government benefits, and permanently erode trust in the American financial system.
2) Disable security safeguards
For the "most transparent government agency ever," Musk and the DOGE crew go to great lengths to cover their digital tracks while accessing information that, if leaked, could destroy U.S.American national security and the economy.
Schneier warned that DOGE routinely disables and deletes any audit trails or logs that would reveal what they're doing to the data behind closed doors. The NLRB whistleblower described in detail the measures DOGE takes to destroy any logs of their activity while on-site at a federal agency.
3) Feed everything into AI
DOGE used an unknown AI tool to create detailed organizational charts of the entire federal government. They even used AI in the decision to fire 300+ nuclear weapons safety experts, a workforce that holds the highest level of security clearance and forms America's last line of defense from invasion. A Department of Energy staffer told CNN,
“The nuclear deterrent is the backbone of American security and stability – period. For there to be any even very small holes poked even in the maintenance of that deterrent should be extremely frightening to people.”
In another disastrous example, a DOGE staffer used AI to make cuts to the nation's largest integrated health care system that serves millions of veterans: the VA. Attempting to take an easy route for cutting veteran care, DOGE's AI identified over 1,000 contracts valued at $34 million dollars each. Except it turns out that was a serious mistake. Experts found that DOGE's AI routinely inflated the cost of flagged contracts by a factor of 10.
Schneier testified:
"Using government data sources to train AI creates a permanent, untraceable record of the data."
4) Outsource control to private companies
What's at Stake: America's Nuclear Umbrella Under Threat
Federal systems face constant attacks from countries like China and Russia, who view our nuclear intelligence and trade secrets as the ultimate prize. Breaches in these areas could cripple the U.S. economy or destroy our nuclear umbrella, eliminating the most fundamental pillar of our defense against invasion.
In February, just one day after 45 terabytes of data left Big Balls' global network, DOGE staffer Luke Farritor gained access to the Department of Energy's IT networks, while SpaceX-turned-DOGE member Ryan Riedel took charge as the nation's nuclear cybersecurity chief. During Riedel's 3-week tenure, waves of Chinese state-backed hackers rampaged through adjacent federal cloud networks at the Treasury Department again . By April, we learned that DOGE had access to two highly-classified nuclear networks, and by July the same set of Chinese cyber threats pulled off a hack against the National Nuclear Security Administration. What's the common thread here? China used specially-developed exploits to hop between different federal agencies' clouds, chaining their attacks to tunnel deeper and deeper into the heart of the U.S. government. During the exact same time period that DOGE had top-level access to the agencies involved.
If Big Balls' network is transferring federal data overseas, it's nearly certain that hostile intelligence agencies have compromised everything in transit. Both Russia and China extensively target U.S. public and private sectors with sophisticated cyberattacks.
Moreover, the open access settings mean other unauthorized hackers could be exploiting these same proxies, creating additional layers of compromise and data theft.
Every day DOGE maintains access to federal systems represents an ongoing threat to American national security.
Parting Words
Perhaps you are thinking to yourself, surely there are grown-ups handling our cybersecurity crisis. Surely, CISA or some other cybersecurity expert in the federal government will see and address this hemorrhaging of sensitive American data to our foreign adversaries. But the core workforce dedicated to defending the U.S. from cyberattacks has been hollowed out by DOGE, and the remaining intelligence analysts have realized there is no higher-up to report these findings to without risking being axed themselves.
If I, as an open source researcher, can collect months of data demonstrating wide-ranging unaddressed national cybersecurity vulnerabilities, then so can any of our foreign adversaries. That said, OSINT will only get us so far; we require a thorough internal investigation to uncover the extent of the damage of DOGE.
The evidence is clear: we are witnessing the largest government data heist in American history, orchestrated by individuals with documented ties to Russian cybercriminals and executed with the full backing of the Trump administration. This goes beyond the risk the risk of your SSN being stolen. It cuts to the very foundation of our national security, from our first line of cyber-defense to our last line of nuclear deterrence.
I need 5 Founder-level subscribers to continue this work.
This article was the result of hours of unpaid time. It’s not behind a paywall because the American people deserve to know the full extent of the national cybersecurity crisis looming before us.
If you can afford it and want to support un-paywalled deep-dive cyber investigations without (too much) jargon, will you become a Founding member or make a one-time donation?
Methodology
For this investigation, I accessed only publicly available servers and metrics requiring no authentication. All server endpoints were publicly accessible at the time of observation. No hacking, credential misuse, or disruption was performed. This analysis involved only passive, open-source monitoring for transparency and public safety.
Questions? Email me at democracy.crescent359@passmail.net
Technical
February 6, 2025 Packetware Kubernetes Cluster-Wide Totals
Total Received: 31.78 TB
Total Sent: 46.75 TB
Net Flow: 14.97 TB egress-heavy
Combined Traffic Volume: 78.52 TB


If you find this work valuable, please consider a one-time donation to keep this investigation going and available for free to the American public.
https://ko-fi.com/defenddemocracy/goal?g=0
This is still happening in real time. You don’t need IT knowledge or access to see what’s going on — look within your own systems processes (civil servants). They’re shoveling data out as quickly as they can, including SSA, NOAA, IRS and others.
The “team” brought on, who allegedly left, are still working within. Ghosts on org charts but they’re very much active and it can easily be proven. All of IT within at least a few Agencies have been consolidated under direct control of these kids. Top-level access and GS-15 ( DC locality) pay with mid-level positions like Front Desk/Office, IT Specialist, etc.
Even SSA’s top systems guy just published whistleblower testimony corroborating details of this post/article. “Big Balls” is one of the lead OCIO employees at SSA, along with at least three others.
Edits - typos